Creating Conditional Statements with Cypher
 How to hack together Neo4j's Cypher statements to conditionally execute code, along with examples of working with API response metadata. Read More ›
How to hack together Neo4j's Cypher statements to conditionally execute code, along with examples of working with API response metadata. Read More ›
Representing Password Reuse in BloodHound
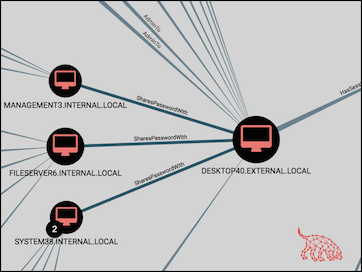 How to integrate password reuse attacks into BloodHound with the 'SharesPasswordWith' relationship. Includes a new Custom Query, API response logic parsing, detailed query output, and more. Read More ›
How to integrate password reuse attacks into BloodHound with the 'SharesPasswordWith' relationship. Includes a new Custom Query, API response logic parsing, detailed query output, and more. Read More ›
Extending BloodHound: Track and Visualize Your Compromise
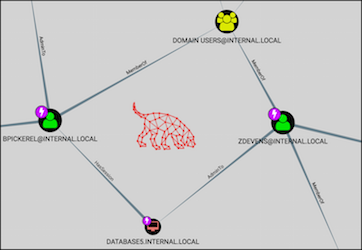 Customizing BloodHound's UI and taking advantage of Custom Queries to document a compromise, find collateral spread of owned nodes, and visualize deltas in privilege gains. Read More ›
Customizing BloodHound's UI and taking advantage of Custom Queries to document a compromise, find collateral spread of owned nodes, and visualize deltas in privilege gains. Read More ›
Using xkeyscan to Parse an X-Based Linux Keylogger
 Leverage native X-based tools for real-time keylogging with xkeyscan, a Python script that translates X keycodes into legible keystrokes. Read More ›
Leverage native X-based tools for real-time keylogging with xkeyscan, a Python script that translates X keycodes into legible keystrokes. Read More ›
Introducing Sleat: Security Logon Event Analysis Tools
 Sleat is a toolkit for weaponizing Windows logs, providing a suite of scripts for collecting, parsing, and analyzing Logon Events. Sleat can perform scope validation, identify exploitation targets for pivoting attacks, visualize network logons, and more. Read More ›
Sleat is a toolkit for weaponizing Windows logs, providing a suite of scripts for collecting, parsing, and analyzing Logon Events. Sleat can perform scope validation, identify exploitation targets for pivoting attacks, visualize network logons, and more. Read More ›